Harmony Platform Security
Jitterbit employs strict security measures to protect our customers’ critical business processes and valuable information.
Jitterbit’s layered security foundation.
Jitterbit is vigilant at applying safe and secure integration processes. We use strict security measures to protect our customers’ valuable information, and constantly evaluate and improve our systems and processes to keep abreast of the latest security demands.
Jitterbit manages the security of the Harmony platform by applying a hybrid framework based on NIST, CISA, CSA, and CERT recommendations. We constantly evaluate and improve our systems and processes to meet or exceed the latest security demands.
This framework is categorized into three key layers: Logical Security, Organizational Security and Physical Security:
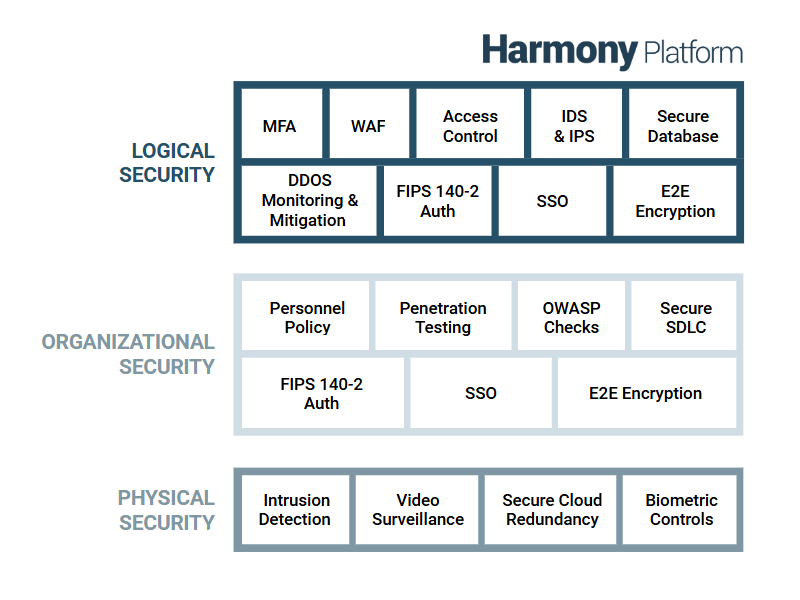
Logical Security
Logical security is comprised of all the security measures taken within the Harmony platform. These include the system architecture; major components; Harmony users, organizations, and roles; Harmony environments and access control; Harmony data storage; and Harmony security topologies.
Organizational Security
Organizational security covers operational best practices of leading cloud-computing providers around the world. This includes confidentiality; the personnel policy; internal team-specific operating procedures and policies; reporting of system status; identity and access management; patch management and high availability; and capacity management.
Physical Security
Physical security involves the hosting of Harmony on cloud infrastructure. This section describes infrastructure compliance; physical and environmental security; high availability and fault tolerance; network security; secure design principles; change management; load balancing security; data storage; and data durability and reliability.
Global accreditation & compliance.
The Jitterbit Harmony platform meets the highest global security standards, and has been accredited by or certified to be compliant with the following global standards:











Read more about our comprehensive security compliance and policies.
View Security PoliciesSecurity Partners






